
Phishing Scams in the Philippines is one of the most dangerous and notorious scams that Filipinos encounter, and continues to be a threat to those unaware. This type of scam is a deceptive trick to obtain a user’s sensitive information such as username, passwords, and even financial information. These malicious practices take form in legitimate emails or websites that trick users into exposing confidential information. These types of scams are notoriously alarming, especially during the upcoming holiday season. In this article, we will tackle how to spot and avoid phishing scams, to help you stay aware and vigilant.
What is a Phishing Scam
Phishing is like a tricky online game that bad actors play to steal your important information. They pretend to be someone trustworthy, like a bank or a popular website, and send you messages that look real. These messages try to make you share your personal details, like passwords or credit card numbers. Falling for their game could lead to big problems, so it’s crucial to recognize these tricks and keep your information safe.
Types of Phishing
While the most common type of phishing is email phishing, there are various types of phishing methods that you should look out for.
Email Phishing
Attackers send fraudulent emails that appear legitimate, often mimicking trusted entities such as banks or government agencies. These emails typically contain malicious links or attachments, aiming to trick recipients into providing sensitive information like passwords or financial details.
Spear Phishing
Spear phishing is a targeted form of phishing where cybercriminals customize messages for specific individuals or organizations. They use information gathered from various sources to make the phishing attempt more convincing and increase the chances of success.
Whale Phishing
Whale phishing, or whaling, focuses on high-profile individuals within an organization, such as CEOs or top executives. Attackers craft sophisticated messages to trick these individuals into divulging critical information or performing actions that could compromise the organization’s security.
Pharming
Pharming involves redirecting users from legitimate websites to fraudulent ones without their knowledge. Attackers manipulate the domain name system (DNS) or use malware to achieve this redirection, aiming to collect sensitive information.
Vishing (Voice Phishing)
Vishing involves fraudulent phone calls, where scammers impersonate legitimate entities, such as banks or government agencies. They use social engineering tactics to extract sensitive information from individuals over the phone.
Smishing (SMS Phishing)
Smishing uses text messages to trick individuals into divulging personal information or clicking on malicious links. These messages often claim urgency or importance to prompt quick responses.
Clone Phishing
Clone phishing involves creating a replica of a legitimate email, but with malicious content. The attacker replaces a legitimate attachment or link with a malicious version, tricking the recipient into thinking it is a genuine communication.
Common Methods of Phishing Scams
These tricky scammers have a few favorite tricks to try and fool you. One of their main plays is sending fake emails that seem real, asking you to click on links or share personal info. Another move is creating fake websites that look just like the real ones you use.
Sometimes, they also trick you with urgent messages, making you feel like you have to act fast. Being aware of these tactics helps you stay one step ahead and avoid getting caught in their schemes.
- Email Phishing
Email phishing is like a sneaky trick where scammers send you fake emails that look real. These emails often pretend to be from trustworthy places like banks or popular websites. They might ask you to click on links or share personal info. Being cautious about unexpected emails and checking if they’re legit helps you dodge this phishing move and keeps your information safe.
- Website Spoofing
Imagine scammers creating fake websites that look exactly like the real ones you trust. That’s website spoofing. They copy the design and layout to trick you into entering your info. Always double-check the website’s address (URL) and make sure it starts with “https://” for a secure connection. By being aware and verifying website details, you can avoid falling into this trap and protect your data.
Pro Tip: To ensure that you’re entering the right website, it is best to search it in Google, rather than clicking untrustworthy links. Most legitimate websites show its ranking at the top of the search results.
- Social Engineering Tactics
Social engineering is like a mind game scammers play. They try to manipulate your feelings or urgency to get you to do something you shouldn’t. It could be pretending to be someone you know or creating a fake emergency. By being aware of these tactics and taking a moment to think before acting, you can outsmart their mind games and keep your personal information safe.
How to Spot a Phishing Scam
One way of preventing yourself or your loved ones from falling to the phishing scam is having the understanding and ability to spot these types of tricks.
Analyzing Suspicious Emails
- Check Sender’s Email Address
When faced with an email that seems fishy, inspect the sender’s email address. Legitimate entities use official domains, so if it looks unusual or doesn’t match the supposed sender, it might be a phishing attempt.
- Look for Generic Greetings
Phishing emails often use generic greetings like “Dear Customer” instead of addressing you by name. Be cautious if the email lacks personalization, as this is a common tactic employed by scammers.
- Examine Email Content for Urgency
Phishers love to create a sense of urgency to make you act without thinking. If the email pushes you to respond quickly or provide sensitive information urgently, it’s a red flag. Take your time and verify before taking any action.
Verifying Website Authenticity
- Check the URL
Before clicking on any links, hover over them to see the actual URL. If it looks suspicious, contains misspellings, or differs from what you’d expect from the legitimate website, it’s safer not to click.
- Look for HTTPS
Ensure the website’s URL starts with “HTTPS://” instead of just “HTTP://.” The “S” stands for secure, indicating that your data is encrypted. A missing “S” could mean the site is not secure.
- Review Website Design and Content
Legitimate websites usually have a consistent design and professional content. If the site you’re on looks amateurish, has strange pop-ups, or deviates significantly from the official site, it might be a phishing page.
A Perfect Example of a Phishing Scam
As mentioned above, phishing scams has three main components: A sense of urgency, a fake email / contact address, and a sketchy link.
Here is a perfect example of a phishing scam look like, provided by Metrobank.
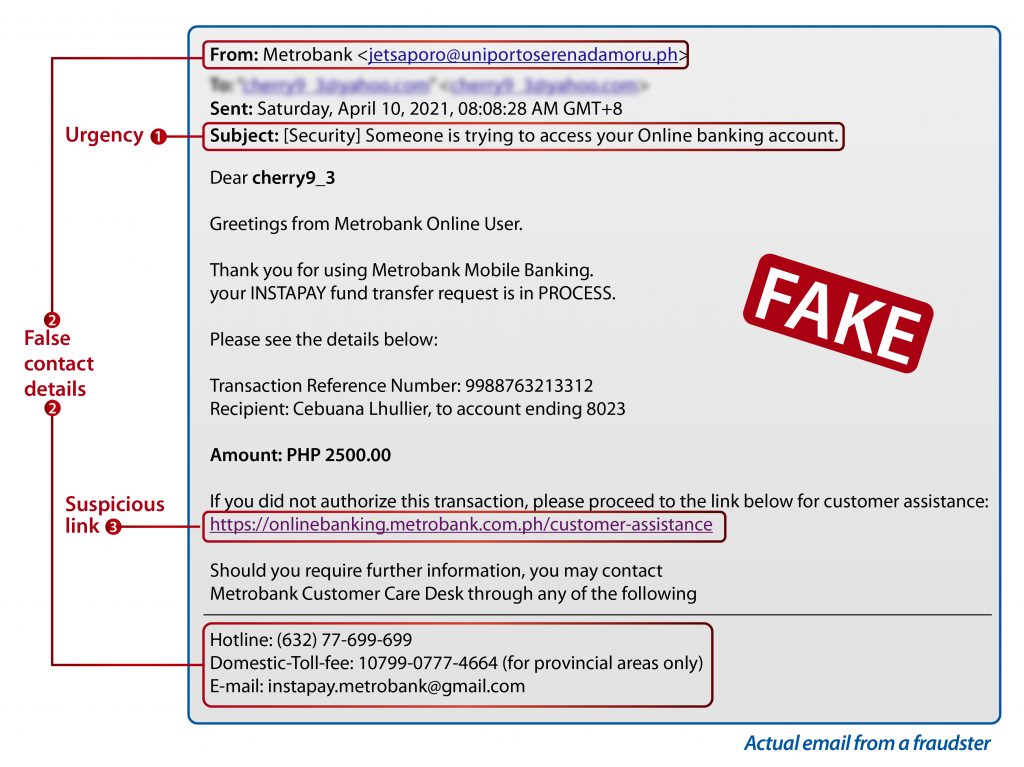
As you can see, the combination of unverified email address, urgency, and suspicious links are present on the phishing email.
Email phishing that impersonates banks or any financial institution is a dangerous scam to fall for. This can lead to a lot of stress, not to mention, your sensitive data such as financial information can be compromised. In the worst case scenario, your hard-earned money may be in jeopardy once scammers get access to your financial information.
Company-related Phishing Attacks
Falling victim to a phishing attack can be particularly damaging, especially for businesses and organizations as it involves financial, reputational, and operational costs.
90% of IT professionals are mainly concerned with Email Phishing. According to a survey conducted by Ironscale.
Another intensive study by IBM in 2022 suggests that Phishing attacks directly contributed to 16% of company data breaches.
On another note, IBM reported that compromised credentials from phishing attacks ranked as the second most expensive source. The global average cost of a data breach in 2023 was USD 4.45 million, a 15% increase over 3 years.
In 2022, Proofpoint‘s analysis revealed that 83% of organizations experienced a successful phishing attempt via email.
Industries or Sectors Commonly Targeted by Phishing Scammers
Phishing scammers cast a wide net, but certain industries or sectors are more commonly targeted due to the potential for financial gain or access to sensitive information.
- Financial Institution
Phishing scammers cast a wide net, but financial institutions remain a prime target due to the potential for significant financial gain. Cybercriminals often orchestrate attacks to obtain sensitive financial information such as login credentials, credit card details, or personal identification numbers.
- SaaS / Webmail
SaaS (Software as a Service) and webmail platforms are also frequently targeted in phishing campaigns. These services often store valuable data, making them attractive targets for scammers seeking unauthorized access to confidential information, corporate accounts, or intellectual property.
- Social Media
Social media platforms are another common focus for phishing attacks, given the vast user bases and the potential for identity theft. Scammers exploit the trust and familiarity associated with these platforms to trick users into disclosing personal information or clicking on malicious links.
- Logistics / Shipping
The logistics and shipping industry, a critical component of global commerce, is not immune to the pervasive threat of phishing attacks. Cybercriminals strategically target this sector, acknowledging the profound impact potential disruptions can have on supply chains and the broader economy. Recognizing the interconnected nature of logistics, these attackers aim to exploit vulnerabilities within the supply chain network, seeking unauthorized access to sensitive shipment information or causing disruptions that can ripple through various industries.
- Ecommerce / Retail
In a digital era dominated by online transactions, the ecommerce and retail sectors have become prime targets for phishing campaigns. Cybercriminals strategically focus on these industries, recognizing the goldmine of valuable data stored within customer accounts and payment information.
The objective often extends beyond mere financial gain, with attackers seeking unauthorized access to online retail platforms. By compromising customer accounts and payment data, these scammers not only threaten the financial security of individuals but also jeopardize the integrity of the entire ecommerce ecosystem, necessitating a robust cybersecurity posture to counter these evolving threats.
- Payment
Payment services, including online payment gateways, are high-priority targets for phishing scammers due to the potential for direct financial theft. Telecommunications companies are also commonly targeted, with attacks aimed at gaining access to sensitive customer data or compromising communication networks.
- Telecommunications
Telecommunications companies are also commonly targeted in phishing attacks, with attacks aimed at gaining access to sensitive customer data or compromising communication networks. The significance of the information held by these companies, coupled with their integral role in communication networks, makes them prime targets for malicious actors seeking unauthorized access.
- Cryptocurrency
Cryptocurrency users and platforms often become targets for phishing attempts, where scammers try to steal private keys, compromise digital wallets, or execute fraudulent transactions. The decentralized nature of cryptocurrencies, which operate without a central authority, adds complexity to securing these assets.
Importance of Awareness against Phishing Cams
“In 2022, the Philippines secured the fifth position among the countries experiencing the highest number of phishing attacks. According to Kaspersky, the Philippines had 4,559,288 phishing incidents recorded in 2022.”
Being aware of phishing scams can save you stress, time, and money. These types of scams are deceptive, and sometimes, we know too little about it. Understanding the deceptive tactics employed by cybercriminals is the first line of defense in protecting personal information. With phishing attempts targeting sensitive data such as passwords and financial details, awareness empowers individuals to recognize and avoid phishing scams. The awareness enables you to prevent potential identity theft and safeguard financial security.
Key Points to Remember about Phishing Scams
- Analyze suspicious emails by checking sender details, avoiding generic greetings, and scrutinizing urgency.
- Verify website authenticity through URL checks, looking for “HTTPS,” and assessing design/content.
- Always triple check the authenticity of the email or website before clicking, visiting, or entering your personal or any sensitive information
Conclusion
It’s clear that phishing scams are a serious matter in the digital landscape in the Philippines. As these scammers get more crafty and creative, it’s up to each of us individuals and our organizations to stay vigilant against these scams. By understanding how these cyber tricks operate, being cautious with emails and websites, and proactively strengthening our defenses, we can collectively create a safer digital space for everyone online.









